Using Sentinel to Hunt for Ransomware Activity in Microsoft 365
Overview
In case your organization falls victim of a ransomware attack, files in Microsoft 365’s cloud storage might be encrypted as well. If users are syncing OneDrive, SharePoint or Teams document libraries with their computers and these machines have become infected by the ransomware, the encrypted files are automatically uploaded to the cloud.
Thanks to Microsoft Sentinel, we can hunt for such ransomware activity and identify all affected document libraries in OneDrive for Business, SharePoint Online and Microsoft Teams. Using Microsoft’s native file version history and ransomware recovery capabilities, we can even restore the document libraries to overcome the attack.
Prerequisites
The following prerequisites must be met to detect malicious file renaming activities in your Microsoft 365 environment and to restore the original document library data in OneDrive/SharePoint/Teams:
- The Office 365 Connector must be activated in Sentinel before the malware incident occurred.
- The version history must be activated for document libraries in SharePoint Online / Microsoft Teams before the malware incident occurred. In OneDrive for Business, versioning is typically enabled by default.
Detect Ransomware with Sentinel KQL Query
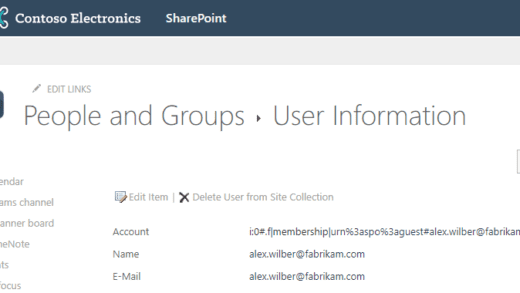
In Sentinel, you can use the following KQL query to search the Office 365 audit logs (OfficeActivity table) for file renaming activities in OneDrive/SharePoint/Teams suspected of being related to a crypto-virus infection.
After encrypting file content, ransomware often also manipulates the file extension. For example, a PowerPoint presentation with extension .pptx might end up in a cryptic .DrtKGUVT_a1BC5-pXYZ format. In particular, the resulting file extension is usually longer than typical file extensions. We use this knowledge to filter our KQL query exactly for file renaming actions that ended up in file extensions with more than 5 characters. Depending on your environment, this approach is too pragmatic. Consequently, to avoid false positives in the query results, we need to filter out some long file extensions from well-known software installed on your clients, such as .cproject from Eclipse projects or the Subversion .svn-base extension. For this purpose, we define an fileExtensionExclusions array. Alternatively, you could maintain a watchlist.
Please find more details on what the Sentinel query does and how you should fine-tune it for your environment directly in the code as follows and in my GitHub repository:
// Define a list of long but well-known file extensions,
// which are not under suspicion of being related to a ransomware attack
// We use this list in the query below in order to remove some false positives
// Please note: You will need to extend this list to exclude further known file extensions used by software in your environment
let fileExtensionExclusions = dynamic(["APACHE", "CATAnalysis",
"CATAnalysisComputations", "CATAnalysisResults", "CATDrawing", "CATPart", "CATProduct", "CATfct",
"FatalErr", "Locking", "SLDASM", "SLDDRW", "SchDoc", "SchDocPreview",
"appinfo", "blend1", "composite", "cproject", "crdownload", "datbackup", "doxyfile", "drawio",
"jsonlz4", "moz-backup", "onetmp", "package", "pbiviz", "project", "properties",
"scoreboard", "svn-base", "tsproj", "whiteboard"]);
// Query the Office 365 audit log
OfficeActivity
// Filter for file renaming activities in OneDrive/SharePoint/Teams, where the file extension has been modified
| where Operation == "FileRenamed"
and SourceFileExtension !~ DestinationFileExtension
// Get the file path of the renamed file but without file extension because we need this to group the query results by each unique file
| extend OfficeObjectIdTrimmedBySourceFileExtension
= substring(OfficeObjectId, 0, strlen(OfficeObjectId) - strlen(SourceFileExtension) - 1)
| extend OfficeObjectIdTrimmedByFileExtension
= iff(OfficeObjectIdTrimmedBySourceFileExtension endswith DestinationFileExtension,
substring(OfficeObjectIdTrimmedBySourceFileExtension, 0, strlen(OfficeObjectIdTrimmedBySourceFileExtension) - strlen(DestinationFileExtension) - 1),
OfficeObjectIdTrimmedBySourceFileExtension)
// Group the results showing each unique file, which is suspected of having been encrypted and renamed by ransomware
| summarize TimeGenerated = arg_max(TimeGenerated, *),
UserId = arg_max(UserId, TimeGenerated),
Site_Url = arg_max(Site_Url, TimeGenerated),
SourceFileName = arg_max(SourceFileName, TimeGenerated),
SourceFileExtension = arg_max(SourceFileExtension, TimeGenerated),
DestinationFileExtension = arg_max(DestinationFileExtension, TimeGenerated),
OfficeObjectId = arg_max(OfficeObjectId, TimeGenerated)
by OfficeObjectIdTrimmedByFileExtension
// Filter for files that currently have an extension with more than 5 characters,
// and which are not contained in our exclusion list of well-known file extensions
// These are the files suspected of being manipulated by ransomware
| where strlen(DestinationFileExtension) > 5
and DestinationFileExtension !in (fileExtensionExclusions)
// Only output the most important properties
| project TimeGenerated, UserId,
Site_Url, SourceFileName, SourceFileExtension,
DestinationFileExtension, OfficeObjectId
// Show the most recent malware renaming activity at the top of the result list
| order by TimeGenerated descThe results table will look as shown on the following image. For each affected file, you can identify the point in time the malicious encryption occurred (TimeGenerated), the user whose machine is infected (UserId), the URL of the affected OneDrive/SharePoint/Teams site (Site_Url), and the name (SourceFileName) + old/new extension (SourceFileExtension / DestinationFileExtension) + full path of the respective file (OfficeObjectId).

Furthermore, you could also store the query as a custom hunting query or analytics rule in Sentinel. Thus, you could periodically search for ransomware activities in Microsoft 365’s cloud storage and you can make sure to be automatically notified via Sentinel incidents as soon as new encrypted files occurred somewhere in OneDrive, SharePoint or MS Teams.
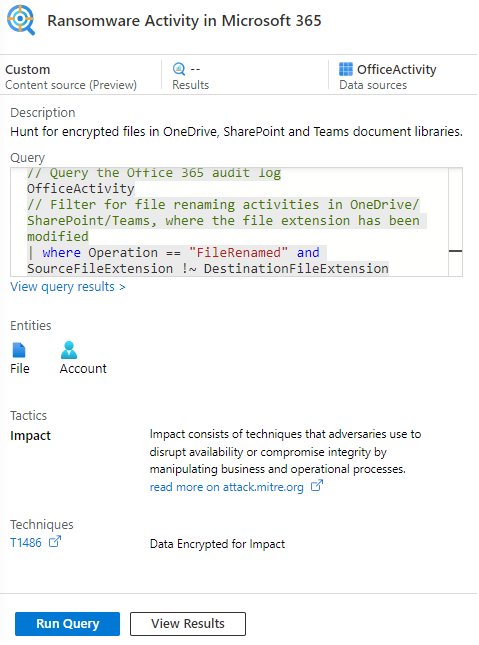
Restore OneDrive, SharePoint and Teams files
Identifying the exact locations where crypto-trojans have been able to tamper with your data is cool, but how to recover from that threat? In case we are talking about encrypted files, which have been synced to the OneDrive/SharePoint/Teams cloud folders, you can benefit from Microsoft’s built-in recovery capabilities. If you have enabled the versioning feature (fortunately, it’s activated by default) in all of the affected document libraries, you can leverage the following documentation to restore your data:
Thus, you can reset all document libraries to a point in time prior to the security incident:
Sources and Further Readings
- Microsoft: Recover from a ransomware attack – Office 365 | Microsoft Learn
- Microsoft: Deploy ransomware protection for your Microsoft 365 tenant | Microsoft Learn
- Microsoft: How to Protect Office 365 with Azure Sentinel – Microsoft Community Hub
- GitHub repository: MicrosoftCloudSecurity/Sentinel/Hunt for Ransomware Activity in Microsoft 365 at main · CloudProtectNinja/MicrosoftCloudSecurity (github.com)